A "one-way valve" for a multi-layered "defense-in-depth" to reduce the blast radius.
The modern operational technology (OT) landscape is at a critical juncture. The once isolated and "air-gapped" networks that control our critical infrastructure—from power grids and water treatment plants to manufacturing floors and transportation systems—are now increasingly interconnected with enterprise IT networks and the broader internet. This convergence, while enabling significant gains in efficiency, data analytics, and remote management, has also exposed these vital systems to an unprecedented level of cyber risk.
Traditional IT security measures, such as firewalls and intrusion detection systems, are essential but often fall short of meeting the unique demands of OT environments. The core challenge lies in the fundamental difference in security priorities. While IT prioritizes the confidentiality of data, OT's paramount concerns are the integrity and availability of the physical processes they manage. A misconfigured firewall or a single compromised software vulnerability could lead to catastrophic physical damage, environmental incidents, or even loss of life.
This is where the data diode, a hardware-enforced unidirectional gateway, emerges as a game-changing security control. This article will expand on the concept of data diodes, providing a deeper dive into their technical architecture, operational benefits, and strategic application within a comprehensive OT cybersecurity framework. We will also explore real-world examples and future trends that solidify their role as a cornerstone of critical infrastructure protection.
Understanding the Technical Underpinnings of Data Diodes: A Deeper Dive
The power of a data diode lies in its deterministic, hardware-based security. Unlike firewalls, which are software-based and rely on a set of rules that can be complex, misconfigured, or exploited by zero-day vulnerabilities, a data diode's security is rooted in the laws of physics.
- Optical Data Diodes: The most common form of data diode technology. The physical isolation is achieved through the use of a fiber optic cable. On the source network side, a transmitter module with a light source (LED or laser) converts digital data into light pulses. These pulses travel through the fiber to a receiver module on the destination network side, which converts them back into digital data. The key design constraint is that the receiver module is a photodiode, which can only detect light and has no capability to transmit. This physical absence of a return path for light fundamentally prevents any data from flowing back. This is not a "firewall rule" to be configured; it is an unchangeable physical reality.
- Electrical Data Diodes: While less common than their optical counterparts, these diodes use specialized electronic circuitry to achieve a similar one-way flow. They might incorporate hardware components, such as solid-state relays or carefully designed transistors, that are physically configured to allow current flow in only one direction. Any attempt to send a signal in the reverse direction is met with an open circuit or a physical block.
- The Protocol Break: This is a crucial concept. Bidirectional protocols like TCP/IP require acknowledgments (ACKs) to confirm the receipt of data packets. A data diode, by its very nature, breaks this loop. The TCP stack on the sending side will send a packet and wait for an ACK that will never come. To overcome this, data diodes are paired with specialized software applications on both the sending and receiving networks. The sending-side software takes the data, “strips” the bidirectional protocol, and transmits it unidirectionally. The receiving-side software then reconstructs the data and presents it to the destination application, often mimicking a bidirectional protocol to the receiving system. This "protocol break" or "deterministic one-way" data transfer ensures that an attacker on the less-trusted network cannot exploit the connection to gain a foothold or issue commands back into the OT network.
Strategic Operational Benefits: Beyond the "One-Way"
While the primary benefit is clear—physical inbound threat prevention—the strategic advantages of data diodes extend far beyond this single point.
- Protection of Legacy Systems: Many OT environments are comprised of legacy systems with outdated operating systems and no patches for known vulnerabilities. An "air gap" has long been the only solution. However, with the need for data and visibility, this is no longer a viable long-term strategy. Data diodes provide a perfect compromise, allowing data to be securely extracted from these vulnerable systems for monitoring and analytics without exposing them to the risks of a live network connection. This extends the operational life of critical assets and avoids the costly and disruptive process of a full system overhaul.
- Regulatory Compliance and Audits: In sectors like energy (NERC-CIP), nuclear, and water, strict regulatory standards mandate the protection of critical systems. The demonstrable physical separation and hardware-enforced nature of a data diode provides a high level of assurance that can satisfy even the most stringent audit requirements. It simplifies the compliance process by offering a security control that is not susceptible to the same human error or software exploits as a firewall.
- Enabling the Industrial IoT (IIoT): The promise of IIoT is the ability to leverage real-time data from sensors and control systems to optimize operations, perform predictive maintenance, and enhance business intelligence. Data diodes are the essential security tool that makes this possible. They enable the secure transmission of sensor data, historian logs, and security event logs from the OT network to the corporate network or a cloud platform for analysis, all while ensuring the OT environment remains impervious to inbound cyber threats. This allows organizations to reap the benefits of IIoT without compromising their most critical assets.
- Reduced Operational Overhead: While the initial cost of a data diode can be higher than a traditional firewall, the long-term operational costs are often lower. There are no complex firewall rules to manage, no logs to continuously sift through for false positives, and no constant patching or maintenance cycles required to address software vulnerabilities. Once the data flows are configured, the data diode operates with a high degree of reliability and minimal intervention.
Data Diodes in Practice: Case Studies and Deployment Architectures
The most effective use of data diodes is not as a standalone solution but as a core component of a defense-in-depth strategy. They are typically deployed at the boundaries between different security zones, particularly where the risk is highest.
Scenario 1: Securing a Historian Server:
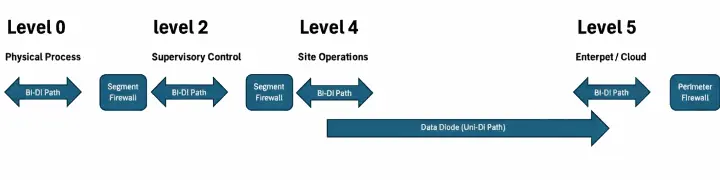
A common use case is to secure the communication between an OT historian server (which collects vast amounts of operational data) and a business intelligence or data analytics server in the IT network. By placing a data diode between these two servers, the IT network can securely pull data for reporting and analysis, but no traffic can ever be sent back, preventing a compromised IT system from poisoning the OT data or launching a lateral attack.
Scenario 2: The Two-Way DMZ Architecture:
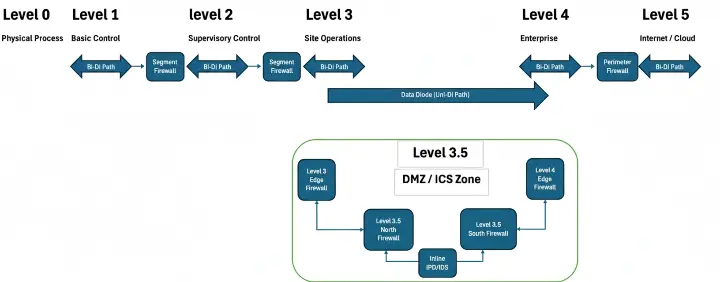
For scenarios that require some form of bidirectional communication (e.g., for patch management or remote access), a data diode is often used in conjunction with a sophisticated demilitarized zone (DMZ) and a series of firewalls. This creates a highly controlled and layered pathway. The data diode handles the secure one-way flow of telemetry data out of the OT network. A separate, four-firewall DMZ architecture is used for on-demand bidirectional access. This setup ensures that the most sensitive data exfiltration is hardware-enforced, while any necessary two-way communication is subject to multiple layers of inspection and control, minimizing the attack surface. Protecting SCADA Systems: In a SCADA environment, data diodes are used to protect the core control systems from external networks. For example, a data diode could be placed between a supervisory control network (Level 3) and a corporate business network (Level 4). This allows operational data and alarms to be sent to a central operations center for monitoring, while ensuring that the critical control commands that could disrupt physical processes cannot be issued from the IT side.
The Future of Industrial Cybersecurity and the Role of Data Diodes
The market for data diodes is projected to grow significantly as organizations in critical infrastructure increasingly recognize the need for hardware-enforced security. Future trends in this space include:
- Expanded Protocol Support: While historically a limitation, modern data diodes and their accompanying software are becoming more sophisticated, with growing support for a wider range of industrial protocols (e.g., Modbus, OPC UA) and cloud-based communication, further enhancing their applicability.
- Integration with AI and Machine Learning: As data diodes securely export operational data, it can be fed into AI and machine learning platforms in the IT network. These platforms can analyze the data for anomalies that indicate a physical security threat or a potential malfunction, enabling predictive maintenance and enhanced threat detection.
- More Accessible Solutions: Historically, data diodes were expensive and complex, reserved for high-security military and government applications. However, as the technology matures and the need for it grows, more affordable and user-friendly "plug-and-play" solutions are entering the market, making this vital security control accessible to a broader range of industrial organizations.
In an era of increasing OT-IT convergence and sophisticated cyber threats, the data diode stands as a powerful and indispensable tool. It offers a level of security that is fundamentally different from traditional software-based controls. By leveraging the immutable laws of physics to enforce one-way data flow, data diodes provide an unbreachable barrier against inbound attacks, protect vulnerable legacy systems, and enable the secure flow of data for modern analytics. They are not a silver bullet, but they are a critical layer in a robust defense-in-depth strategy, ensuring that as we build an increasingly connected and automated society, we do so with a foundation of uncompromising security and resilience.