In today's digital world, passwords are a weak link. We're all tired of remembering complex combinations, and they're easily guessed, stolen, or phished. While they've served us for decades, it's time for a more modern, secure approach. Enter Certificate-Based Authentication (CBA), a powerful method that uses cryptography to secure access for users and devices.
This article will explore what CBA is, how it works, and why it's a superior alternative to traditional passwords and other authentication methods.
What is Certificate-Based Authentication?
At its core, CBA is a security mechanism that uses a digital document called a certificate to verify identity. Unlike a password, which is a secret you know, a certificate is something you have—a digital credential issued by a trusted third party known as a Certificate Authority (CA).
These certificates contain a user's or device's public key, identity details, and an expiry date, all sealed with the CA's digital signature. This cryptographic approach makes CBA incredibly difficult to compromise.
How Does CBA Work? A Simple Flow
The process of authenticating with a certificate is both straightforward and highly secure.
Certificate Issuance: A user or device requests a certificate from a trusted CA. After verifying their identity, the CA issues the certificate, which includes the public key.
Authentication Request: When the user or device wants to access a resource (like a server or network), it presents its digital certificate as proof of identity.
Server Validation: The server receiving the request performs a series of checks:
Is the certificate signed by a trusted CA?
Is it still valid (not expired or revoked)?
Does it match the requesting user or device?
Challenge-Response (Optional but Recommended): To prevent replay attacks, the server can send a random "challenge." The client uses its private key (which is never shared) to digitally sign this challenge. The server then uses the public key from the certificate to verify the signature.
Access Granted: If all checks pass, the server grants access.
Enhanced Security and Privacy: The Core Benefits of CBA
While passwords rely on a human's ability to remember a secret, CBA is built on the robust foundation of Public Key Infrastructure (PKI). This cryptographic system is the backbone of its security, offering profound advantages.
1. Phishing-Resistant by Design
The biggest security advantage of CBA is its inherent resistance to phishing attacks. With passwords, attackers trick users into entering their credentials on a fake website. Once the password is stolen, the attacker can use it to access the real account.
With CBA, this attack vector is eliminated. The private key used for authentication never leaves the device. It is not something the user can type or be tricked into giving away. The authentication process happens cryptographically behind the scenes between the device and the server, making it immune to credential theft through phishing.
2. Stronger Identity Assurance
A password only proves that someone knows a secret. That secret can be shared, stolen, or brute-forced. A digital certificate, however, cryptographically binds an identity (user or device) to a unique public key. This provides stronger identity assurance because the authentication is based on a unique, non-guessable cryptographic key pair.
3. Mutual Authentication and Trust
Unlike many password systems where only the user authenticates to the server, CBA can enable mutual authentication. This means both the client (user/device) and the server verify each other's identity. Before the client sends its certificate, it first validates the server's certificate. This prevents man-in-the-middle attacks, where an attacker impersonates the server to intercept communication. By verifying both parties, CBA builds a secure, two-way trust relationship.
4. Zero-Trust Security Model
CBA is a perfect fit for a zero-trust security model, which operates on the principle of "never trust, always verify." Every user and device, whether inside or outside the network, must authenticate. By requiring a unique, cryptographically-signed certificate for every connection, CBA ensures that only known and trusted entities can access resources, minimizing the attack surface.
5. Enhanced Privacy
CBA provides a significant privacy benefit by not exposing any sensitive credentials. Unlike passwords which are transmitted (even if encrypted) or stored in databases (hashed), the private key is never transmitted. This means there's nothing for an attacker to intercept, even if they breach a server, as the private keys are never stored there. This reduces the risk of mass data breaches exposing user credentials.
CBA vs. Passwords and Tokens: A Head-to-Head Comparison
CBA isn't just an alternative; it's a significant upgrade. Here's a quick comparison to highlight its strengths.
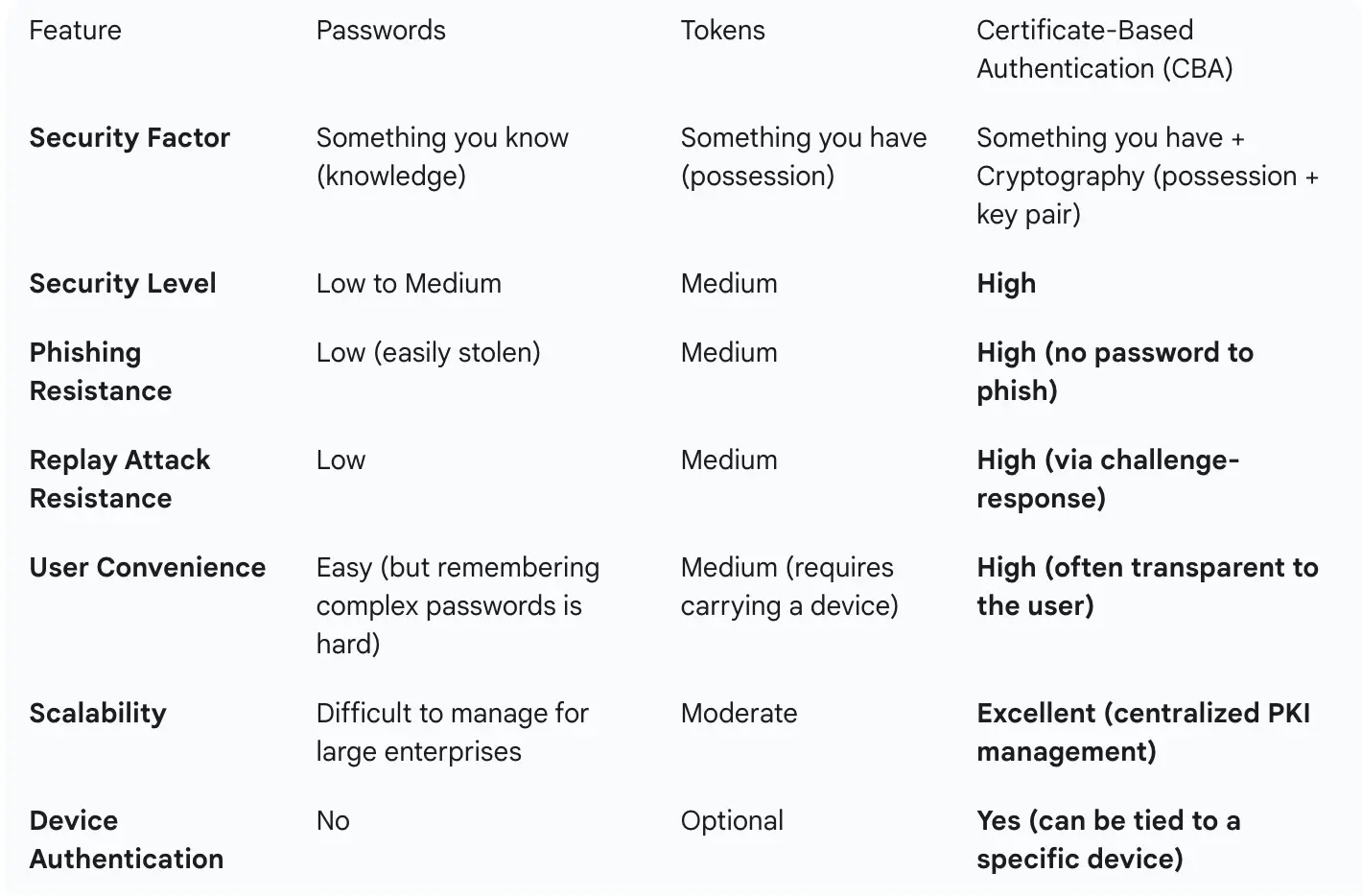
Where is CBA Used?
CBA is becoming the standard for modern security in a variety of applications:
VPN Access: Secure remote access by ensuring only authenticated devices can connect.
Secure Wi-Fi: WPA2/WPA3 Enterprise networks use certificates to authenticate devices.
Web Servers: The "S" in HTTPS (Secure Sockets Layer) is powered by certificates that verify the server's identity.
IoT Devices: Ensures that only trusted devices can join and communicate on a network.
Enterprise Applications: Many modern cloud services and internal portals are shifting to passwordless logins using certificates.
Why CBA is the Way Forward
By leveraging the power of cryptography, CBA solves the core problems of traditional passwords. It eliminates the risk of weak or stolen credentials, prevents common attacks like phishing and replay, and provides strong device validation with enhanced privacy.
For any organization or system requiring strong, scalable security, adopting CBA is no longer just a good idea—it's a critical step toward a passwordless, more secure future.